This article is based on actual events. For those who don’t know me personally, let’s say that I am a zero-trust freak. I am writing this article to prove that sometimes common sense is more important than any anti-malware. Keep reading for further information.
A good friend recently told me he received a problematic email with a strange file attached. He was wise enough not to click on the suspicious file and called me to check it together. I know he is a tech-aware person, so if he tells me he suspects something, then it most likely is. Long story short, he was. Let’s see how some scams might trick you, and even your anti-malware is not adequate on some occasions.
The suspicious email
We all know that when we receive an email from an unknown source, it is better to ignore it or be very cautious. That’s true if you don’t use it for business purposes. My friend runs a company, so receiving emails from unknown senders is not strange. The said email was well-written and seemed to be from a legitimate company. The domain was in question, but it is not unusual for big companies to send emails from third-party domains (still suspicious). He exchanged more emails with the “company’s representative,” and we reached the hard rock point.
The suspicious attached file
As mentioned, the emails were well-written, had good-quality images, and the domain looked quite normal—until he received an email with a suspicious file attached. It seemed to be a financial contract, but its extension was “.exe.” Exe files are executable files. There is no reason for a contract to be an executable file rather than a PDF. And this is where I kick in.
The analysis
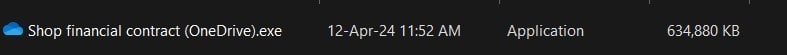
From now on, something was odd. Things were suspicious. The first thing we did was to scan the file with two different well-regarded anti-malware tools. Both found nothing malicious. Still, an executable contract is not something you expect to see, especially from a well-known brand. So, we continued by uploading the file to the VirusTotal site (please refer to my article for further information). The file was about 620 MB, which also rings a bell. Cyber-criminals make large files to make it more difficult to be scanned, depending on your anti-malware scanner’s configuration. As VirusTotal is a notorious tool, exceeding the maximum upload limit is what they are looking for. Recently, it was changed from a 550 MB max upload limit to 650 MB. So, we were lucky enough not to exceed the limit (620 MB file).
After VirusTotal analysis, we were informed that eight anti-malware engines (now there are more) identified it as a generic trojan file. Generic Trojans are not so alarming since it means that it might be a false positive. The most challenging part was that only three of them were trusted tools. So, it was not something to worry about too much, but it still was uncomfortable. Eight identifications are not in a comfy zone, but it is also a matter of heuristics/ false positive/ tuning of every anti-malware engine. Some anti-malware tools offer only what they consider optimal to VirusTotal because bandwidth is also critical. So, it is not unusual to have different results.
Still, I have to analyze it further. The next step was to open the file in a hex editor. A hex editor is an excellent way to see if something is wrong with a file. There are portable editors, so installing them on your rig is unnecessary. I was curious to know why the file was so large. Cyber-criminals, most of the time, fill a file with zeros to enlarge it. Zeros are the optimal way to enlarge it without affecting the malicious code, which might be a few kb in size. And that’s precisely what it was revealed. The actual code was only 8 MB after deleting all the zeros.
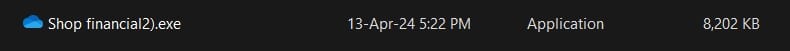
A legit program rarely has so many zeros because that makes it unnecessarily large. And that is something alarming. Uploading only the stripped-down version of the file in VirusTotal was more revealing now. More engines identified it as a threat, which makes it suspicious. It was about time to say goodbye to our malicious friend. The worst part was our time spent on a scam, and what could have happened if my friend wasn’t cautious enough. Even the best might fall victim, but it is best not to. Common sense is essential, as well.
The lesson
The lesson is simple. Anti-malware tools and common sense are the perfect combination. Anti-malware tools are essential, but nothing is guaranteed if you aren’t cautious enough. Trust nothing that might ring a bell even if your tool doesn’t identify it as a threat. If something seems too alarming, then it might be malicious. This article is a perfect example of this. The following rules are simple:
- Always be cautious with an unknown email or an email by a known sender that doesn’t seem normal.
- Always check the domain of the email (smartphones unfortunately don’t reveal the full address)
- Check the general quality of the images and the text.
- It is best to check the file extension of the attachment. Be cautious if it is different from what it is meant to be. For example, large PDF files, files that are meant to be PDF files but have different extensions (e.g., jimckd.pdf.exe, which .exe is the real extension of the file), etc.
- If a file seems suspicious, seek help from someone who knows, or don’t click on it without further information. If you think that would be best, you can contact the legitimate sender for more assurance.
- Never trust your anti-malware tool unquestioningly. It is best to scan a suspicious file with different tools. The VirusTotal site is also helpful.
- Report them to the appropriate official anti-fraud organizations for the US and EU.
- Common sense or anti-malware alone is not enough. Both of them combined are the best practice.
There is a proverb that says: Curiosity killed the cat. Unfortunately, we all might be that cat someday, somehow. Better safe than sorry is the best practice. As always, stay safe and stay in the know.


Excellent Article!
Excellent advice and recommendations for dealing with malware and staying safe.
Thank u very much. The purpose was to be informative. I think it is. 🙂