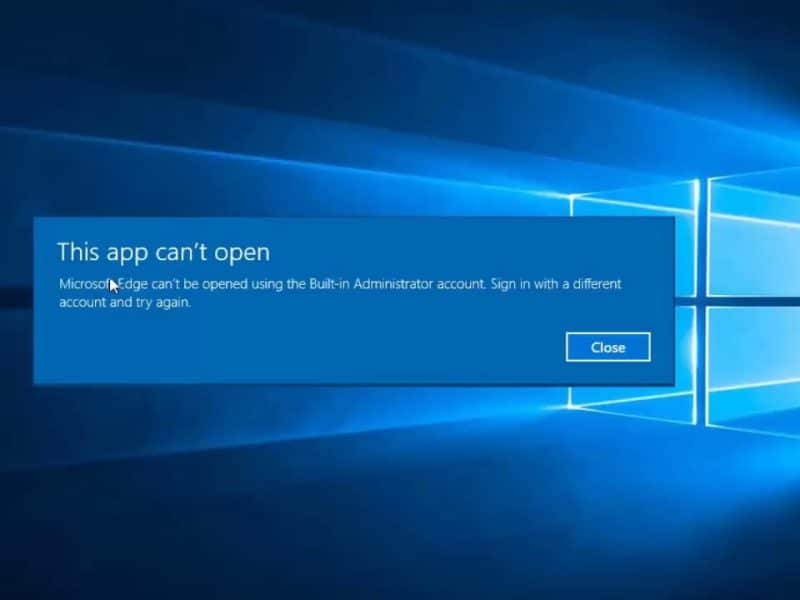
Imagine you have some serious stuff to do. You fire up your PC, and Windows Desktop welcomes you as usual. You double-click on the app
Author: JimCKD

Laser projection keyboards sound like the next big thing in gadgets. This might be true if you are willing to pay a street price for

Auto SR (not to be confused with DirectSR), Microsoft’s own-baked AI image upscale feature, is available on Windows 11 ARM devices. That means that if

Andreas Constantinides has over 20 years of extensive experience in cybersecurity and IT, holding various managerial and supervisory roles. Currently, he serves as Manager of
Windows offers convenient ways to handle our PC power on/off—hibernation, sleep, shut down, restart, etc. Many of us prefer the “Shut down” option. But complete

FL STUDIO MOBILE is the mobile version of FL STUDIO Desktop DAW. For those who don’t know already, FL Studio (formerly known as FruityLoops from
Intel recently announced more details about its upcoming Lunar Lake CPU architecture, which is expected to launch in Q3 of this year. Moreover, according to

Comicdom CON (established by Comicdom Press) is one of the most well-regarded annual cultural festivals in Athens. It is free to join and offers a

We have to admit it. Programs are valuable tools for our convenience. But sometimes choosing the right program might be challenging if we don’t know

Safe Mode is one of the most valuable tools when troubleshooting a Windows device. It loads the OS only with the absolute minimum and necessary